Microsoft defender for multicloud
Microsoft defender for multicloud
Multicloud computing refers to the use of multiple cloud computing services from more than one cloud provider (including private and public clouds), in a heterogeneous environment. A multicloud strategy provides greater flexibility, and mitigates risk. Choose services from different cloud providers that are best suited for a specific task, or take advantage of services offered by a particular cloud provider in a specific location.
GCP authorization design The authentication process between Microsoft Defender for Cloud and GCP is a federated authentication process.
When you onboard to Defender for Cloud, the GCloud template is used to create the following resources as part of the authentication process:
Workload identity pool and providers
Service accounts and policy bindings
The authentication process works as follows:
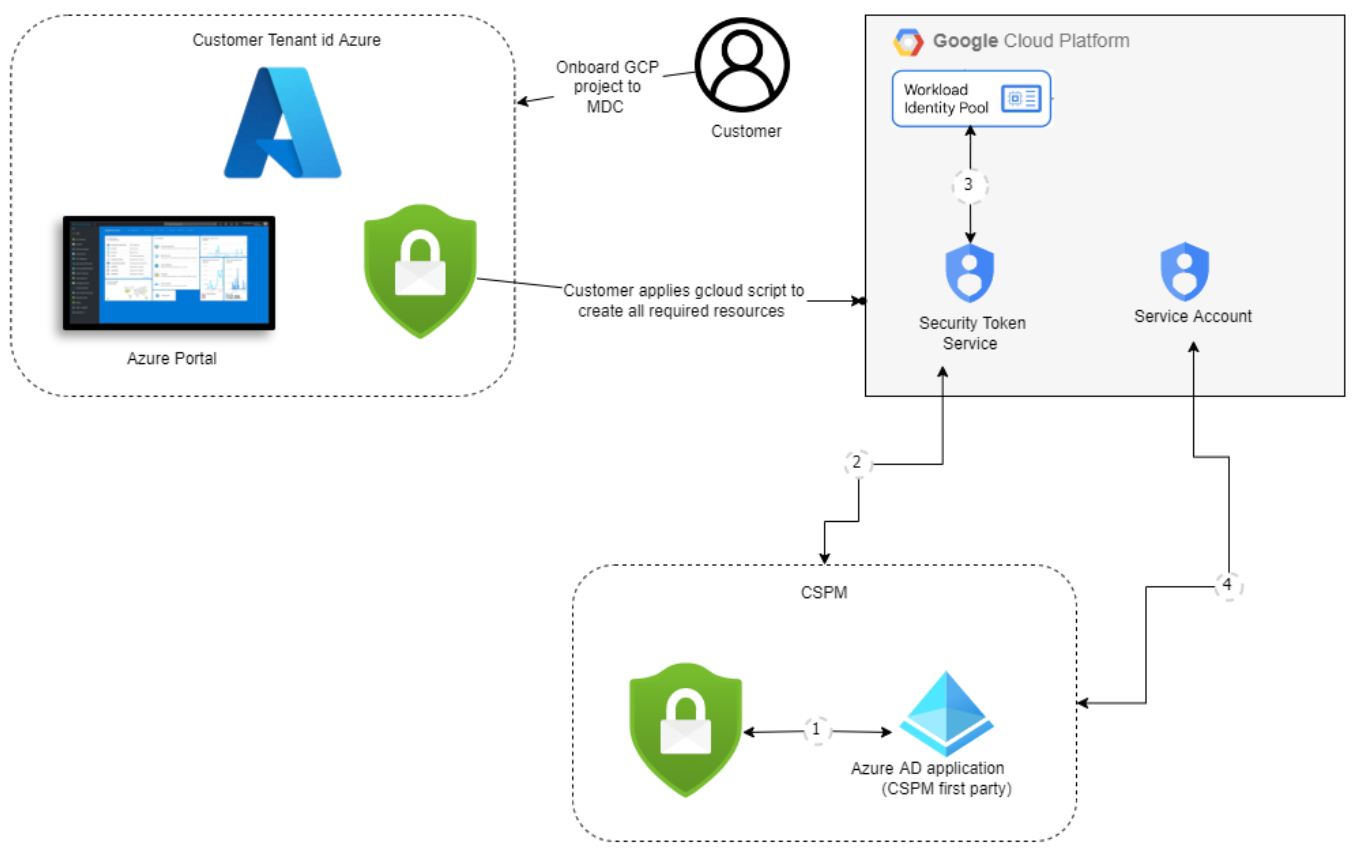
(1) - Microsoft Defender for Cloud's CSPM service acquires a Microsoft Entra token. The token is signed by Microsoft Entra ID using the RS256 algorithm and is valid for 1 hour.
(2) - The Microsoft Entra token is exchanged with Google's STS token.
(3) - Google STS validates the token with the workload identity provider. The Microsoft Entra token is sent to Google's STS that validates the token with the workload identity provider. Audience validation then occurs and the token is signed. A Google STS token is then returned to Defender for Cloud's CSPM service.
(4) - Defender for Cloud's CSPM service uses the Google STS token to impersonate the service account. Defender for Cloud's CSPM receives service account credentials that are used to scan the project.
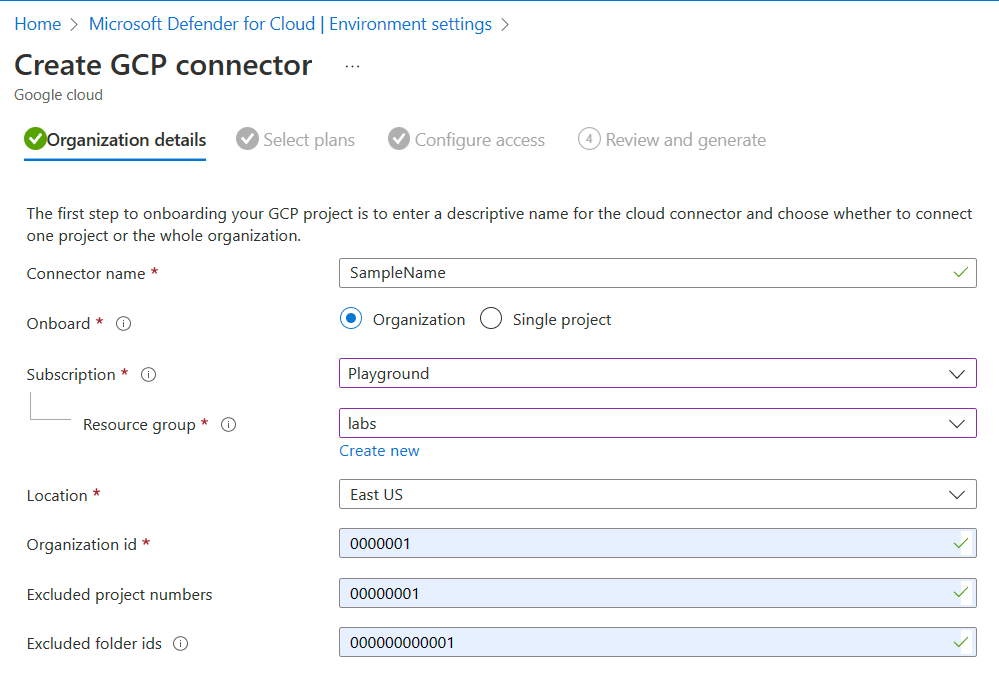
select plan
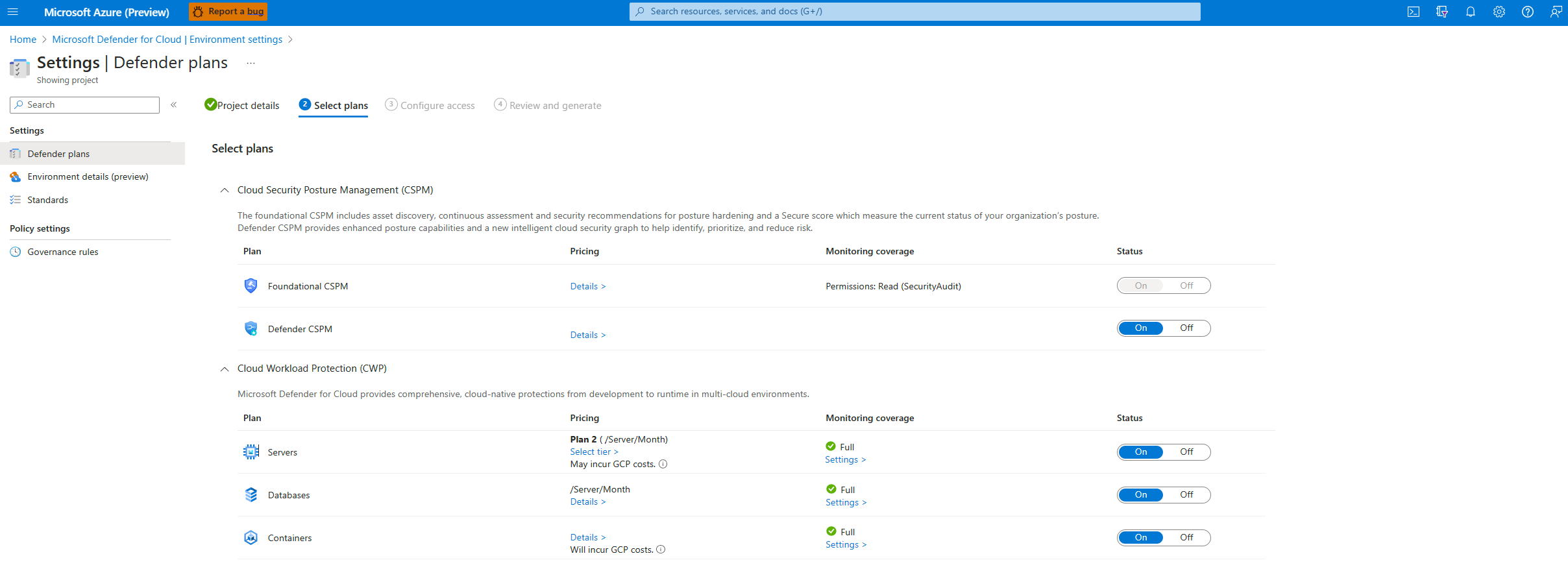
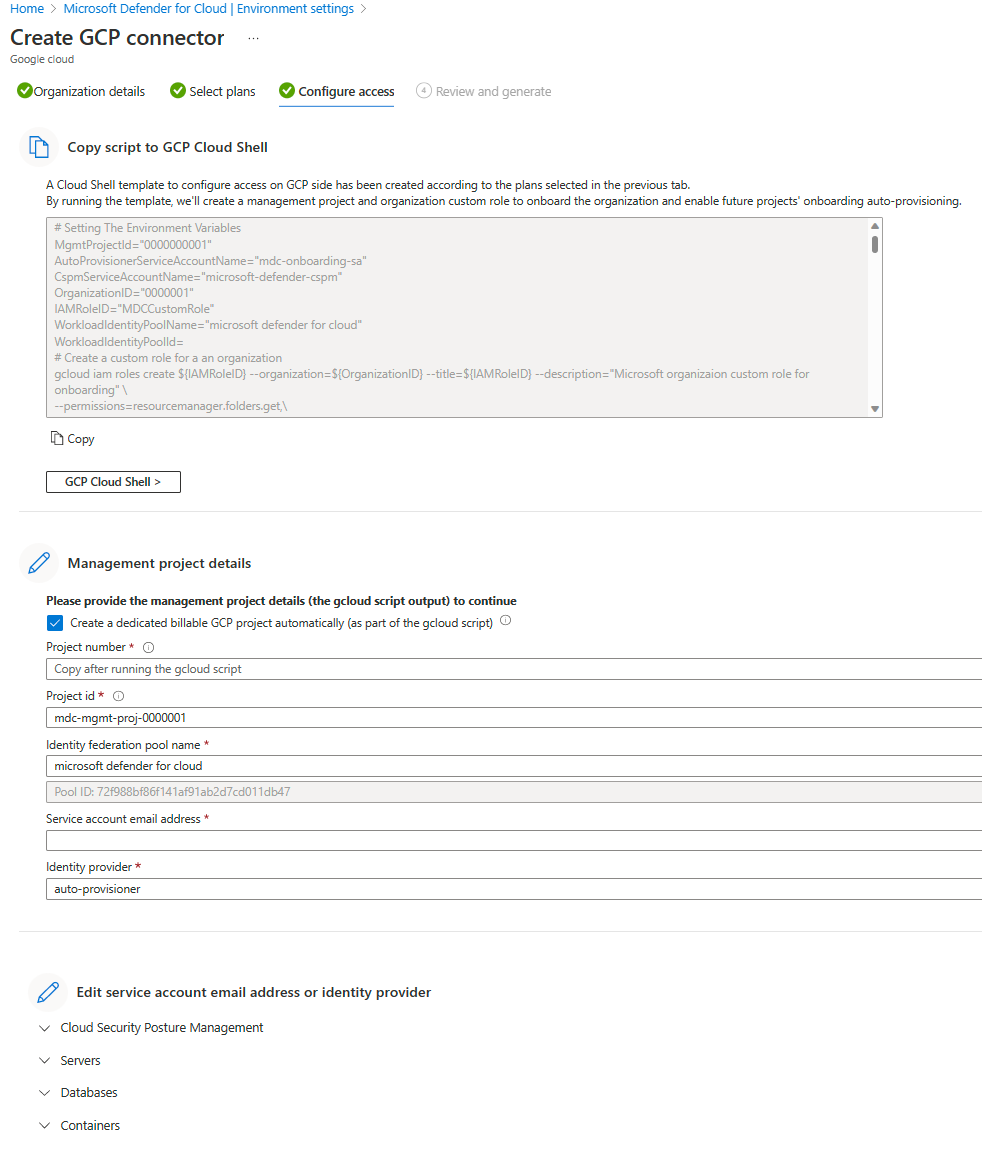
Configure access
Defender for Cloud's AWS connector To protect your AWS-based resources, you must connect your AWS account using the built-in connector. The connector provides an agentless connection to your AWS account that you can extend with Defender for Cloud's Defender plans to secure your AWS resources: If you are connecting an AWS account that was previously connected with the classic connector, you must remove them first. Using an AWS account that is connected by both the classic and native connectors can produce duplicate recommendations.
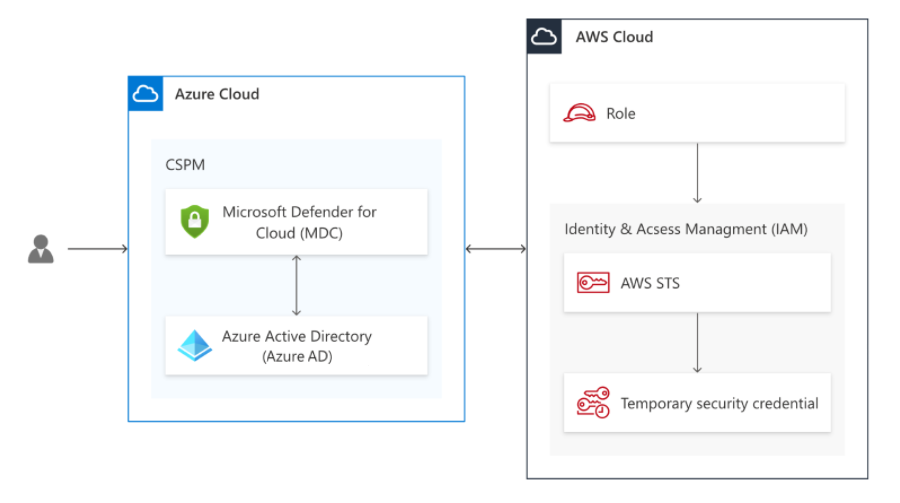
Zero Trust infrastructure and integrations
Zero Trust is a security strategy for designing and implementing the following sets of security principles:
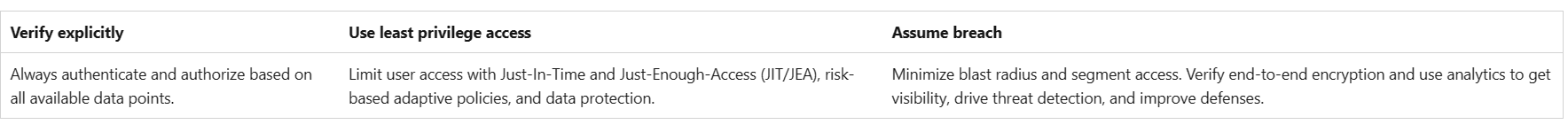
Zero Trust and Defender for Cloud Our Zero Trust infrastructure deployment guidance provides key stages of the Zero Trust strategy for infrastructure. Which are:
Assess compliance with chosen standards and policies Harden configuration wherever gaps are found Employ other hardening tools such as just-in-time (JIT) VM access Set up threat detection and protections Automatically block and flag risky behavior and take protective actions
Refrence from- Microsoft https://learn.microsoft.com/en-us/azure/defender-for-cloud/zero-trust
