Create and upload certificates with zero trust
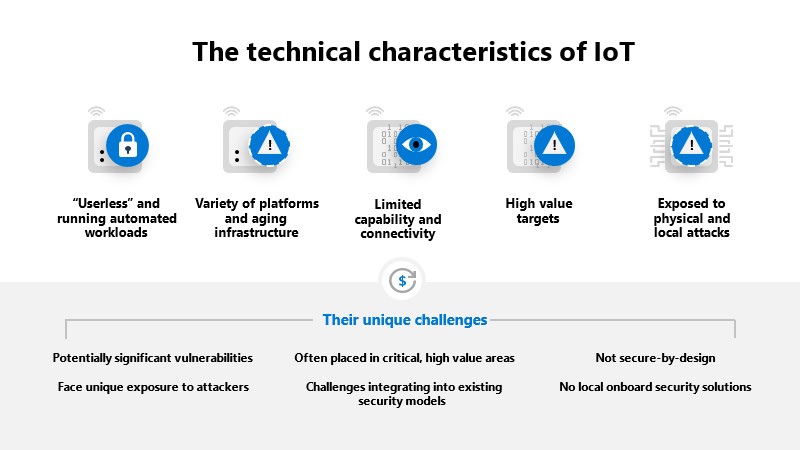
Technical characteristics of IoT and their challenges
Once those requirements are met, we can shift our focus to the specific Zero Trust requirements for IoT solutions:
- Strong identity to authenticate devices. Register devices, issue renewable credentials, employ passwordless authentication, and use a hardware root of trust to ensure you can trust its identity before making decisions.
- Least privileged access to mitigate blast radius. Implement device and workload access control to limit any potential blast radius from authenticated identities that may have been compromised or running unapproved workloads.
- Device health to gate access or flag devices for remediation. Check security configuration, assess for vulnerabilities and insecure passwords, and monitor for active threats and anomalous behavioral alerts to build ongoing risk profiles.
- Continual updates to keep devices healthy. Utilize a centralized configuration and compliance management solution and a robust update mechanism to ensure devices are up to date and in a healthy state.
- Security monitoring and response to detect and respond to emerging threats. Employ proactive monitoring to rapidly identify unauthorized or compromised devices.
Key Zero trust highly capabilities
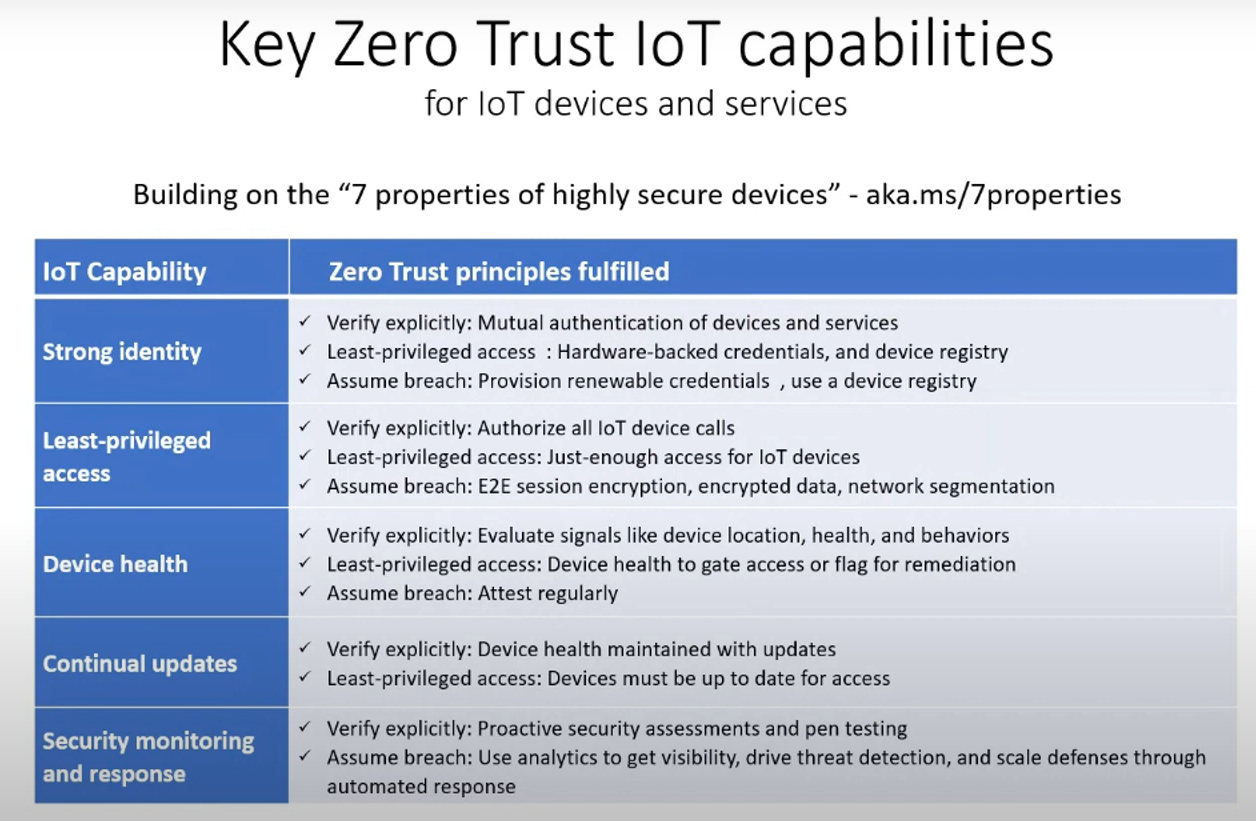
Refrence from :- https://www.microsoft.com/en-us/security/blog/2021/05/05/how-to-apply-a-zero-trust-approach-to-your-iot-solutions/
Create and upload certificates for testing
You can use X.509 certificates to authenticate devices to your IoT hub. For production environments, we recommend that you purchase an X.509 CA certificate from a professional certificate services vendor. You can then issue certificates within your organization from an internal, self-managed certificate authority (CA) chained to the purchased CA certificate as part of a comprehensive public key infrastructure (PKI) strategy. For more information about getting an X.509 CA certificate from a professional certificate services vendor, see the Get an X.509 CA certificate section of Authenticate devices using X.509 CA certificates.
The following tutorial uses OpenSSL and the OpenSSL Cookbook to describe how to accomplish the following tasks:
- Create an internal root certificate authority (CA) and root CA certificate
- Create an internal subordinate CA and subordinate CA certificate, signed by your internal root CA certificate
- Upload your subordinate CA certificate to your IoT hub for testing purposes
- Use the subordinate CA to create client certificates for the IoT devices you want to test with your IoT hub For more information and refrence:-
https://learn.microsoft.com/en-us/azure/iot-hub/tutorial-x509-test-certs?tabs=windows
https://github.com/dotnet/samples/blob/main/iot/dotnet-iot-and-nanoframework/create-certificate.md
