Step for configure azure iot age module in device
Configuring an IoT Edge module on a device involves several steps to ensure proper deployment and functionality. Below is a general guide that outlines the steps for configuring an IoT Edge module:
1. Set Up Azure IoT Hub: Create an Azure IoT Hub, which will serve as the central messaging hub for communication between IoT Edge devices and the Azure cloud. 2. Register a Device in IoT Hub: Register the specific device in the Azure IoT Hub to establish a connection between the device and the IoT Hub. 3. Install IoT Edge Runtime on the Device: Install the Azure IoT Edge runtime on the target device. This runtime facilitates the deployment and execution of modules on the edge device.
Setting up the Raspberry Pi
- Raspberry Pi (RPi) is running Raspbian Stretch
- Install Docker and Docker Compose on the Raspberry Pi
- Install Azure IOT Edge Runtime
- Register Microsoft key and software repository feed
curl https://packages.microsoft.com/config/debian/stretch/multiarch/prod.list > ./microsoft-prod.listsudo cp ./microsoft-prod.list /etc/apt/sources.list.d/ curl https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor > microsoft.gpg sudo cp ./microsoft.gpg /etc/apt/trusted.gpg.d/
- Installing Moby-Engine, and IOTEdge Runtime on linux
sudo apt-get update sudo apt-get install moby-engine
sudo apt-get install iotedge
Docker Compose: If you are using Docker Compose to define and run multi-container Docker applications, you can define the IoT Edge services in your docker-compose.yml file.
version: '2'
services:
yourmodule:
image: yourmodule:latest
restart: always
ports:
- "5000:5000"
environment:
- MODULE_NAME=yourmodule
- UpstreamEdgeHubConnectionString=${UpstreamEdgeHubConnectionString}
Configure RPi with IoT Edge and Connection String
sudo nano /etc/iotedge/config.yamlprovisioning: source: "manual" device_connection_string: "<YOUR_CONNECTION_STRING>"
Restart the IoT Edge runtime to apply the changes:
sudo journalctl -u iotedge -f
Verify Connection:
sudo journalctl -u iotedge -f
4. Create IoT Edge Solution: Develop an IoT Edge solution that includes the necessary modules. This can be done using tools such as Visual Studio Code or Azure IoT Explorer.
5. Configure Module Twin Properties: Define the desired properties and configurations for your IoT Edge module in its twin. This configuration is used to control the behavior of the module.
6. Define Module Deployment Manifest: Create a deployment manifest that specifies which modules will run on the IoT Edge device, their version, and the desired properties. 7. Deploy Modules to Edge Device: Deploy the IoT Edge solution to the target device. This triggers the deployment of the specified modules and their configurations.
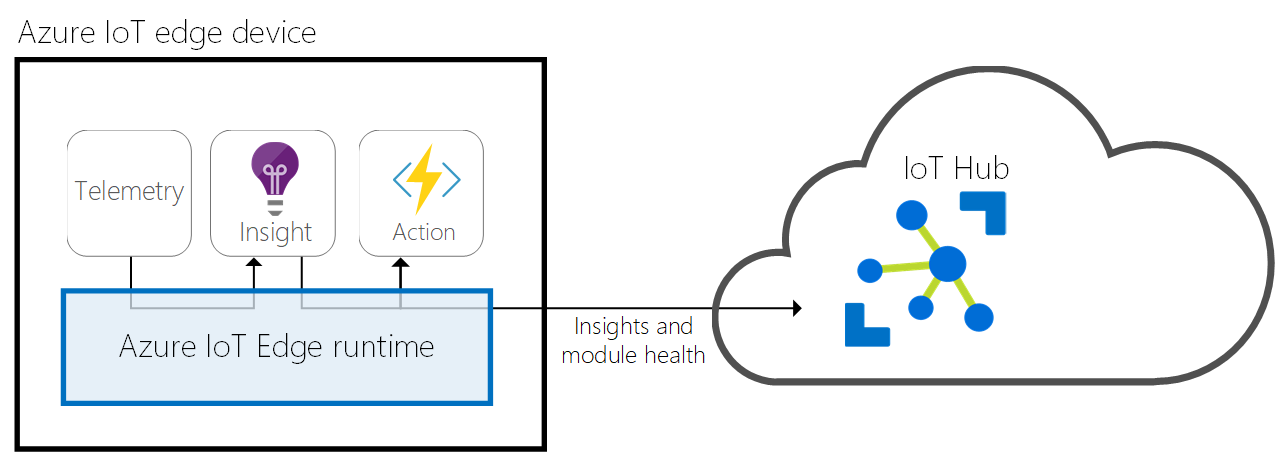
Cloud Communication
8. Monitor Module Status: Monitor the status of the deployed modules to ensure that they are running as expected on the edge device. This can be done through Azure Portal, Azure IoT Explorer, or other monitoring tools.
9. Handle Module Communication: Implement communication logic within the modules to send and receive messages from other modules or the Azure cloud. This involves using appropriate protocols and APIs.
10. Update Module Configuration: If needed, update the configuration of the deployed module by modifying its twin properties and triggering a new deployment.
Module using routing
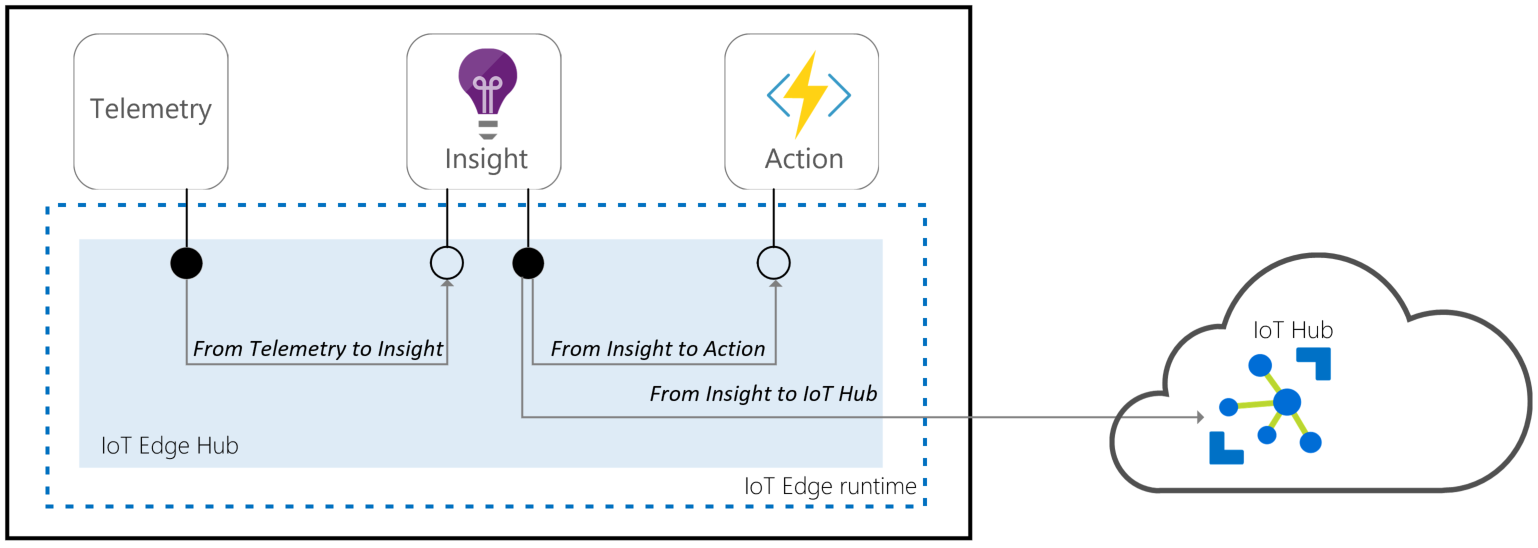
11. Handle Errors and Debugging: Implement error handling mechanisms within the module code and use debugging tools to troubleshoot issues during deployment or runtime.
12. Implement Security Measures:
Ensure that proper security measures are in place, including secure communication channels, device authentication, and access control.
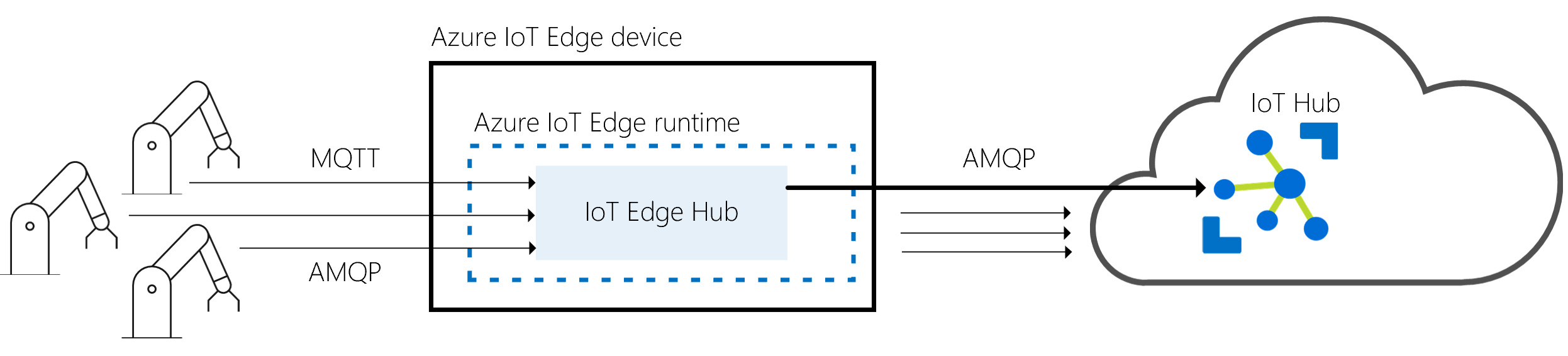
IoT Edge hub supports clients that connect using MQTT or AMQP. It does not support clients that use HTTP.
When a client connects to the IoT Edge hub, the following happens:
If Transport Layer Security (TLS) is used (recommended), a TLS channel is built to establish an encrypted communication between the client and the IoT Edge hub. Authentication information is sent from the client to IoT Edge hub to identify itself. IoT Edge hub authorizes or rejects the connection based on its authorization policy.
By default, the IoT Edge hub only accepts connections secured with Transport Layer Security (TLS), for example, encrypted connections that a third party can't decrypt.
If a client connects on port 8883 (MQTTS) or 5671 (AMQPS) to the IoT Edge hub, a TLS channel must be built. During the TLS handshake, the IoT Edge hub sends its certificate chain that the client needs to validate.
13. Documentation: Document the configuration settings, deployment process, and any custom logic implemented in the IoT Edge module for future reference.
14. Testing: Conduct thorough testing of the entire IoT Edge solution to verify that modules are interacting correctly and delivering the expected functionality.